IT Security Services
JANAH AL MADINA IT SERVICES managed Security Services keep your IT network and device ecosystem safe and secure. We help you stay ahead of cyber criminals by keeping your IT environment updated and respond quickly to threats before your security is breached.
- 24 X 7 X 365: Your network is secured all day, every day
- End-To-End: Complete network and device coverage for optimal protection
- Comprehensive: We cover end-point security as well as information, event, device, vulnerability and access management
- Compliance: We follow ITIL v3 based delivery process
Read more
IT Management Services
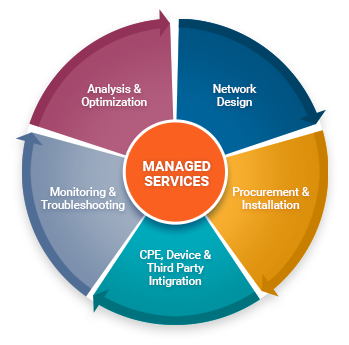
IT management services are primarily used for managing the network environment of an organization and are typically delivered by a third party or external IT service provider under a formal contract or service agreement. These services can include enterprise network management, monitoring, security, capacity planning, performance monitoring, continuous technical support, etc.
Typically, IT management services are performed on the in-house or enterprise-owned IT infrastructure. However, this can also include the service provider's or another third party IT service platform, resources or infrastructure.
Read more
Backup & Data Recovery
JANAH AL MADINA IT SERVICES offers fast, easy, and reliable data backup and recovery services for a wide variety of enterprise applications, ensuring robust and vigorously maintained data safeguards.
Data Protection
We develop innovative cloud data protection solutions to protect our customers data on a wideset & diverse workload systems.
VMware Integration
We offer VMware integrations to ensure flexible and consistent data protection across the VM container and other application environments.
Cyber Recovery
We engineer data backup & recovery solutions that perform data recovery and protect critical data from ransomware and cyber attacks.
Read more
Cloud Managed Services
The capabilities of the Cloud There a reason cloud adoption has been one of the major shifts in the last few years. Companies have discovered that with its inherent flexibility and scalability, cloud technology makes it possible to power the applications, file-sharing and mobility requirements essential to running a modern workplace.
Our Cloud Services allow organizations to move their workloads to a secure cloud environment where they can easily scale as their business grows, paying only for what they need, when they need it. Companies can setup and deploy applications on All Covered state-of- the-art Cloud Servers without having to build or maintain the infrastructure themselves and making them available to customers anywhere at Fires, floods and natural disasters are often unavoidable, but that doesn’t mean your organization has to be unprepared.
Cloud infrastructure As a Cloud services provider to manage resources includes several aspects of cloud computing such as load balancing, performance, storage, backups, capacity, deployment etc…
- Infrastructure as a Service (IaaS)
- Platform as a Service (PaaS)
- Software as a Service (SaaS)
- Identity as a Service (IDaaS)
- Network as a Service (NaaS)
Read more
Big Data And Analytics
Big data analytics helps businesses and organizations make better decisions by revealing information that would have otherwise been hidden.
Our cloud servers and server farms have met the most stringent norms for security, accessibility, protection and privacy. This gives us a chance to keep your information sheltered, agreeable with your industry& controls, and accessible to your office and affirmed remote gadgets through a secured Internet association. Cloud computing which we can access the applications use over the internet. It allows us to create, configure, and customize the business applications online. They are different types deploying applications in to cloud, it is depends on your business requirements. Like Data Security and Privacy Requirement, Budget Requirements, which Type of cloud use want to integrate in public, private and both in hybrid, Data backup, Training, Dashboard and reports, Client access requirements, Data export requirements, We helps you small, medium and enterprise before migrating the entire business to cloud.
Read more
Application Management
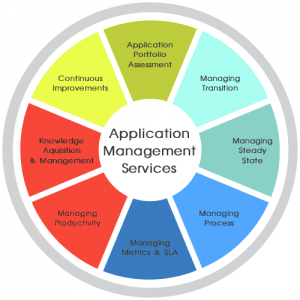
Application administration (AM) is the procedure of dealing with the operation, upkeep, forming, and servicing of an application for the duration of its life-cycle. AM incorporates best practices, methods and methodology fundamental to a sent application’s ideal operation, execution, and proficiency all through the endeavour and back-end IT base.
What Makes JANAH AL MADINA IT SERVICES Unique
Our outsourcing groups are one of a kind blend of industry, IT, information driven, and innovation skill. By keeping up a steady, experienced group acquainted with your applications, surroundings, and business practices, we’re ready to give a comprehensive way to deal with improving and redesigning your frameworks. This extensive, client driven methodology takes into account day by day operational backing while likewise giving application specialists ready to create and send improvements that keep your applications up to speed with your advancing business necessities. Our group has the mix of both specialized and business skill to give custom-made answers for streamline esteem for your business.
Read more
Cyber Security

Cyber security is the application of technologies, processes and controls to protect systems, networks, programs, devices and data from cyber attacks. It aims to reduce the risk of cyber attacks and protect against the unauthorised exploitation of systems, networks and technologies.
Read more